Introducing Private Deployments in Estuary Flow
We are excited to announce the launch of Private Deployments, a highly requested enterprise feature in Estuary Flow that sets a new standard for secure data management. This feature brings the full power of Flow to mission-critical private cloud deployments.
What Are Private Deployments?
Private Deployments offer a robust and secure way to manage your data by allowing you to deploy Estuary Flow’s data infrastructure within your private environment while maintaining the simplicity and efficiency of our SaaS platform.
This feature is designed to give you complete control over your data pathways, ensuring compliance with the most stringent data security requirements.
Benefits of Private Deployments
- Private Cloud: Meet your security and governance requirements by deploying your data, network, and compute within your private cloud.
- Improved Productivity: Get all the benefits of SaaS in your own environment. With private deployments, Estuary Flow is deployed as a cloud-native private data plane in minutes, and managed by a centralized, easy-to-use SaaS control plane that cannot access your data.
- Increased Performance: Provision dedicated, isolated tenancy connectors and compute to help ensure the performance, scalability, and reliability you need for your data pipelines, without getting impacted by others.
- Lower Networking Costs and Latency: With private deployments, you can enjoy zero egress fees and lower latency.
- Complete Control: You determine where to deploy your data infrastructure—whether in Estuary's secure cloud or your own environment. This flexibility ensures that your data management practices align with your organizational policies and compliance needs.
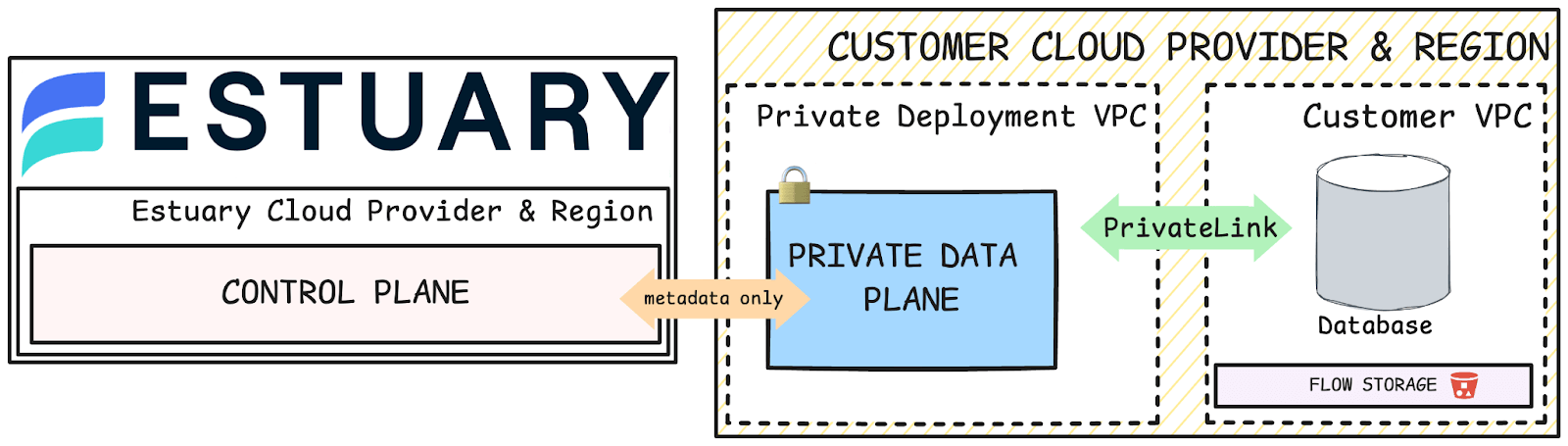
How It Works
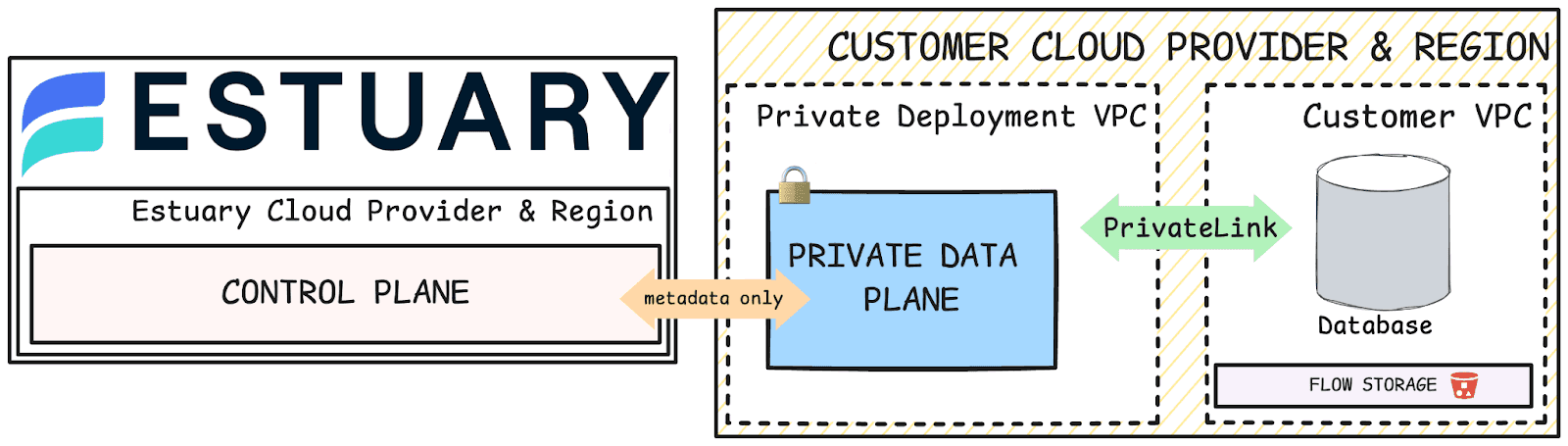
Estuary Flow separates the control plane from the data plane to enhance security and manageability. Users can create a private data plane on the Estuary Flow dashboard and assign connectors to the new data plane. Tasks, which include captures, derivations, and materializations, can be deployed to both public and Private Deployments from the same account.
The architecture is designed to ensure that your data stays within your private network as it moves through your data pipeline. This design supports moving data planes across regions, ensuring consistent security measures regardless of geographic location.
Commitment to Security and Compliance
Our infrastructure is built on hardened Ubuntu 22.04 instances, complying with industry standards such as SOC 2. We implement extensive security measures to harden worker nodes, ensuring a robust and secure environment for data processing.
From kernel module hardening to logging and auditing, every aspect of our infrastructure is designed to protect against a wide range of threats. This comprehensive approach ensures that your data is managed in a secure and compliant manner, providing peace of mind in an increasingly complex data landscape.
Join Us on This Journey
Explore Private Deployments in Estuary Flow today and experience a new level of secure data management. For more details, visit our documentation page or contact our support team.
Thank you for being part of the Estuary community. We are excited to continue this journey with you, delivering cutting-edge solutions that empower your data-driven success.
Stay connected with us on LinkedIn, Twitter, and Substack for the latest updates and insights.

About the author
Dani is a data professional with a rich background in data engineering and real-time data platforms. At Estuary, Daniel focuses on promoting cutting-edge streaming solutions, helping to bridge the gap between technical innovation and developer adoption. With deep expertise in cloud-native and streaming technologies, Dani has successfully supported startups and enterprises in building robust data solutions.
Popular Articles